Impersonations and Business Email Compromise (BEC) Scams
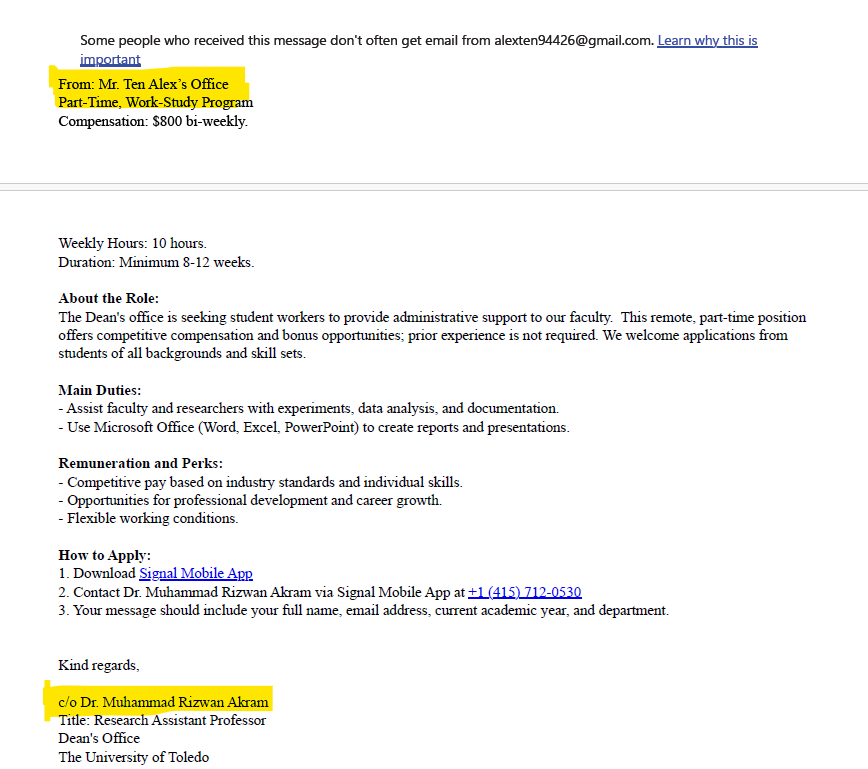 Cybercriminals are increasingly using impersonation tactics—posing as trusted colleagues,
administrators, or partners—to trick people into sharing confidential information
or transferring funds. These Business Email Compromise (BEC) scams are highly targeted
and often very convincing. A single successful attempt can impact academic departments,
research projects, or healthcare operations. Verifying requests and recognizing warning
signs helps the campus community defend against these schemes.
Cybercriminals are increasingly using impersonation tactics—posing as trusted colleagues,
administrators, or partners—to trick people into sharing confidential information
or transferring funds. These Business Email Compromise (BEC) scams are highly targeted
and often very convincing. A single successful attempt can impact academic departments,
research projects, or healthcare operations. Verifying requests and recognizing warning
signs helps the campus community defend against these schemes.
Recognizing BEC Scams
- Unexpected requests for payments or sensitive info.
- Slightly altered email addresses.
- Urgent, high-pressure language, asking to download the attachments or visit the webpage.
Protection Tips
- Confirm requests through separate communication channels.
- Be cautious with links or attachments.
- Report suspicious emails immediately.


